[Q1-Q8] Download Free Microsoft 70-742 Exam Questions And Answers From Lead2pass
Lead2pass Dumps For Exam 70-742 With New Updated Exam Questions:
https://www.lead2pass.com/70-742.html
QUESTION 1
You have a server named Server1 that runs Windows Server 2016.
You need to configure Server1 as a Web Application Proxy.
Which server role or role service should you install on Server1?
A. Remote Access
B. Active Directory Federation Services
C. Web Server (IIS)
D. DirectAccess and VPN (RAS)
E. Network Policy and Access Services
Answer: A
QUESTION 2
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com.
The forest contains a member server named Server1 that runs Windows Server 2016.
All domain controllers run Windows Server 2012 R2.
Contoso.com has the following configuration.
PS C:\> (Get-ADForest).ForestMode
Windows2008R2Forest
PS C:\> (Get-ADDomain).DomainMode
Windows2008R2Domain
PS C:\>
You plan to deploy an Active Directory Federation Services (AD FS) farm on Server1 and to configure device registration.
You need to configure Active Directory to support the planned deployment.
Solution: You raise the domain functional level to Windows Server 2012 R2.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Device Registration requires Windows Server 2012 R2 forest schema (not just domain schema).
QUESTION 3
Your network contains an Active Directory forest named contoso.com.
The forest contains a single domain. The domain contains a server named Server1.
An administrator named Admin01 plans to configure Server1 as a standalone certification authority (CA).
You need to identify to which group Admin01 must be a member to configure Server1 as a standalone CA. The solution must use the principle of least privilege.
To which group should you add Admin01?
A. Administrators on Server1.
B. Domain Admins in contoso.com
C. Cert Publishers on Server1
D. Key Admins in contoso.com
Answer: A
QUESTION 4
You network contains an Active Directory domain named contoso.com. The domain contains 1,000 desktop computers and 500 laptops.
An organizational unit (OU) named OU1 contains the computer accounts for the desktop computers and the laptops.
You create a Windows PowerShell script named Script1.ps1 that removes temporary files and cookies.
You create a Group Policy object (GPO) named GPO1 and link GPO1 to OU1.
You need to run the script once weekly only on the laptops.
What should you do?
A. In GPO1, create a File preference that uses item-level targeting.
B. In GPO1, create a Scheduled Tasks preference that uses item-level targeting.
C. In GPO1, configure the File System security policy. Attach a WMI filter to GPO1.
D. In GPO1, add Script1.ps1 as a startup script. Attach a WMI filter to GPO1.
Answer: B
QUESTION 5
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest named contoso.com.
The forest contains a member server named Server1 that runs Windows Server 2016.
All domain controllers run Windows Server 2012 R2.
Contoso.com has the following configuration.
PS C:\> (Get-ADForest).ForestMode
Windows2008R2Forest
PS C:\> (Get-ADDomain).DomainMode
Windows2008R2Domain
PS C:\>
You plan to deploy an Active Directory Federation Services (AD FS) farm on Server1 and to configure device registration.
You need to configure Active Directory to support the planned deployment.
Solution: You upgrade a domain controller to Windows Server 2016.
Does this meet the goal?
A. Yes
B. No
Answer: A
QUESTION 6
Your network contains an Active Directory domain named contoso.com.
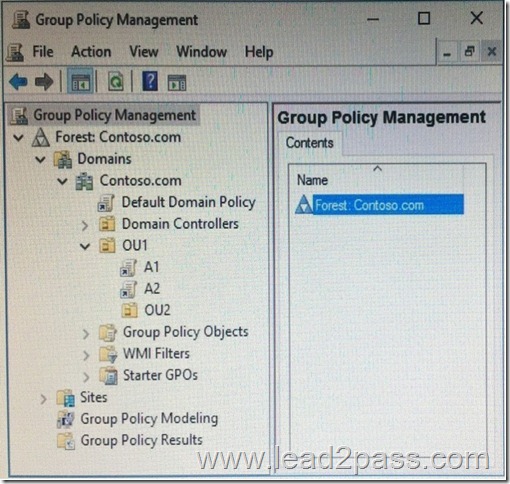
You open Group Policy Management as shown in the exhibit. (Click the Exhibit button.)
You discover that some of the settings configured in the A1 Group Policy object (GPO) fail to apply to the users in the OU1 organizational unit (OU).
You need to ensure that all of the settings in A1 apply to the users in OU1.
What should you do?
A. Enable loopback policy processing in A1.
B. Block inheritance on OU1.
C. Modify the policy processing order for OU1.
D. Modify the GPO Status of A1.
Answer: C
QUESTION 7
Your network contains an Active Directory domain named contoso.com.
You have an organizational unit (OU) named OU1 that contains the computer accounts of two servers and the user account of a user named User1.
A Group Policy object (GPO) named GPO1 is linked to OU1.
You have an application named App1 that installs by using an application installer named App1.exe.
You need to publish App1 to OU1 by using Group Policy.
What should you do?
A. Create a Config.zap file and add a file to the File System node to the Computer Configuration node of GPO1.
B. Create a Config.xml file and add a software installation package to the User Configuration node of GPO1.
C. Create a Config.zap file and add a software installation package to the User Configuration node of GPO1.
D. Create a Config.xml file and add a software installation package to the Computer Configuration node of GPO1.
Answer: C
QUESTION 8
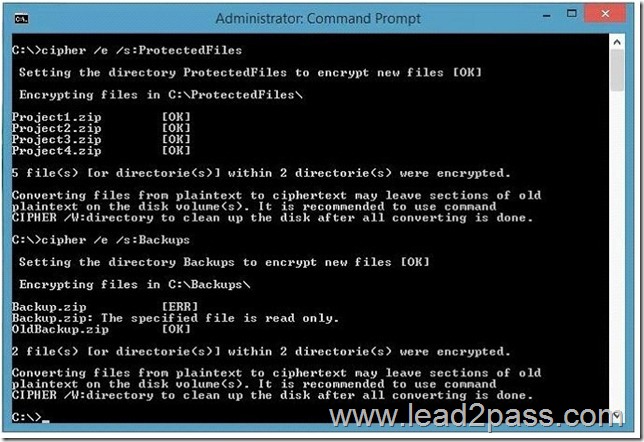
You deploy a new enterprise certification authority (CA) named CA1.
You plan to issue certificates based on the User certificate template.
You need to ensure that the issued certificates are valid for two years and support autoenrollment.
What should you do first?
A. Run the certutil.exe command and specify the resubmit parameter.
B. Duplicate the User certificate template.
C. Add a new certificate template for CA1 to issue.
D. Modify the Request Handling settings for the CA.
Answer: B
70-742 dumps full version (PDF&VCE): https://www.lead2pass.com/70-741.html
Large amount of free 70-742 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDRWlFSW1vN0JwT3M
You may also need:
70-740 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDMXFQVl9VSWx5WGs
70-741 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDb05IRmRaei1JLVE
70-743 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDdjVzVlJxOXB5TTg
70-744 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDVExYaWZyTWt4OGc